Today I put in production on my secondary Internet connection the new Cisco 877 Integrated Services Router. Since the previous model was quite older (C837), I’m pretty impressed by the power of this new machine, which features a fully managed 4 ports FastEthernet switch. Thanks to VLAN support, this router will even be able to survive to the current ADSL line, since I can easily configure one FastEthernet port to be the WAN interface.
All unmatched great features of the Cisco IOS 12.4T bring this router among ones best priced in the SME market.
Drupal 6
Some days ago our production web application platform has been upgraded to the 6.9 Drupal release. A little work has been necessary to migrate some self-customized themes and to remove or substitute with custom views some modules which were not available for the 6.x branch.
Drupal has confirmed to be a very interesting web development framework to address the needs of highly customized and business-tailored applications for (at least) the SME segment.
Blogging on the road
This is the first post I can write without being in front of a computer: I’m using my new iPhone to write these lines while I’m “on the go”! 🙂
I must admit that I never thought to blog in that way, but this mobile device seems a very powerful platform, not only because of it’s builtin functions, but mainly because of the possibilities it can offer by the development point of view. This post is a little example of what I mean: I wrote it using a thirdt party application developed by the WorPress team who made it available on the Apple online App Store.
CommuniGate in production
The migration process I began some days ago to the new CommuniGate Pro platform has successfully completed today. Surely, a lot of things might be improved, but all the majour features needed by our internal corporate usersare just available.
Some troubles were encountered in porting old calendar and contact data from the old system, but we have managed to fill all the gaps we encountered by now. The new system will allow us to consolidate both asyncronous and syncronous collaboration services (such as mail, calendar, contacts, presence, IM and even VoIP) into one single, robust, dependable, highly scalable and secure Unix server.
We are trying the Mailshell SpamCatcher plugin to filter the spam remaining after all incoming messages have been inspected by our Sendmail frontend servers, and it seems to be quite a good alternative to the Exchange Intelligent Message Filter which is based on Microsoft’s SmartScreen technology.
This work makes up the biggest step towards a broader migration process to technologies and products out the Microsoft’s world, since the Redmond’s software house missed the promise to bring its customers to reliable but cost effective IT solutions. Quite all today’s products from Microsoft are unreliable and cost-prone both in implementation and management terms.
CommuniGate upcoming
Today I officially began the path towards the migration from Microsoft Exchange to the Stalker’s CommuniGate Pro platform. A lot of time has past since I discovered this piece of software, but what I learned about it in the past months has convinced me to put it in production. CommuniGate has a lot of strenght points which make it a good alternative (even better on many aspects) to the Microsoft’s mail server. I can’t obviously write them all now, but the reliability gained by this software’s architecture (which comes from simplicity) can be enough to persuade a lot of Exchange2k7-sceptic sysadmins to give a look at it.
I’m currently running CommuniGate 5.2.6 on a FreeBSD 7.0/amd64 jail. By now on, all SMTP traffic flow from/to my corporate domains is routed by this server. As soon as I go on the migration process, all contents from Exchange private and public stores will be gradually moved to CGP, until the Exchange host will be left emptied and will be decommissioned. Corporate users whose mailbox has been migrated can already use the new Pronto! web interface by using the URL https://mail.valsania.it/Pronto.
First WPMU upgrade
Today I got the time to upgrade the WordPress MU platform which is running the Valsania Corporate Blogs collection from version 1.5.1 to the release 2.6 (which is based on WordPress 2.6). It has been the first time I upgrade a WPMU instance in a production envirnoment. The upgrade procedure has been extremely straightforward, and I must say I’m quite impressed by that, since my WPMU configuration is very complex (many plugins and customizations were made, but all of them should have been made consistently with the architecture). At the same time I got all the others WP-based blogs I manage upgraded to the 2.6.1 release.
wpDirAuth 1.4 patch
Today I had to login into one of my WP powered weblogs, running the wpDirAuth 1.3 plugin which I wrote about in this previous post. Surprisingly, it returned me the error message “No directory server available for authentication”. No change was made in the last few days in my infrastructure, and I soon discovered that all user accounts in my Active Directory were able to succesfully authenticate with the only exception of mine!
A few minutes have been necessary to understand that the problem was lying in the password I changed yesterday, which was including an apostrophe (‘). It seems that the function parsing this variable in WordPress automatically puts a backslash (\) escape character before the apostrophe, in order to pass it correctly to the builtin authentication function. The matter was the way the ldap_bind() PHP function was sending the password to my domain controllers, including the unnecessary (in this case) escape character.
I’m not a developer, but I think I resolved this issue, simply by adding the line in bold to the wpDirAuth_bindTest() function in the file wpDirAuth.php:
function wpDirAuth_bindTest(&$connection, &$username, &$password)
{
   $password = strtr($password, array(“\'”=>”‘”));
   if ( ($isBound = @ldap_bind($connection, $username, $password)) === false ) {
     // @see wpLDAP comment at http://ashay.org/?page_id=133#comment-558
     $isBound = @ldap_bind($connection,”uid=$username,$baseDn”, $password);
   }
   return $isBound;
}
Since the returned error message was also incorrect (it should be a “check credentials” warning, not a “server unreacheable” error), I’ve also included the change suggested by Clint in the last part of his message “I have a bug fix for 1.3…“.
I’ve also succesfully tested this modified wpDirAuth plugin against different Active Directory instances on WordPress 2.6 and I’ve genereted two patch to upgrade from both 1.2 and 1.3 version. Here are the links:
If you prefer to use directly the 1.4 release I’ve also prepeared a pre-patched copy that you can download it here.
Since that’s not my job, I’m not sure to have done a good thing by defining this as the new 1.4 release, and I’ll be glad to receive any suggestion about it.
Mac work in progress
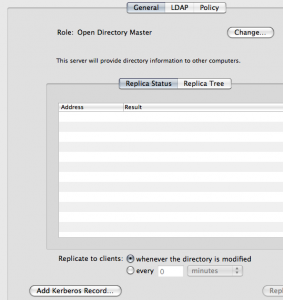
It’s impossible to keep an updated list of what I’m studying about the latest Apple technologies, but today I’ve successfully completed a “milestone” step towards the integration of OD in a Microsoft AD environment, and I must to write it somewhere.
An essential step in the process of migrating from MSFT to Apple IT infrastructure is the setup of a Mac OS X Server as Open Directory Master, leveraging the KDC service of an existing Active Directory Domain Controller. It’s just a snap to make this new server join a Microsoft-based realm and then installing OD services on it to take advantage of the centrally managed authentication from AD while effectively managing all Mac client with the MCX (Managed Client for XÂ ) system.
What it took me into some troubles was the integration of the AFP (Apple Filing Protocol) service that I need to host Mac users’ home folders into the Microsoft customized Kerberos infrastructure. At the end I only needed to issue the command “dsconfigad -enableSSO” on the Mac server to have all Mac users automatically authenticated through Kerberos TGS (Ticket Granting Service) released by Microsoft’s KDC. Chances are that this behavior was due to a little bug in the Server Admin interface, which didn’t show me the button to join an external Kerberos realm under the OD Service settings tab, since the same machine was acting as an Open Directory Master, as you can view in the next figure.
Now, by using the same AD credentials whichever machine they log on to, my users browse happily both SMB and AFP shares, without being prompted for the same password after the first Kerberos authentication. Another little step was done through the way of adopting Apple technologies in the enterprise.
Corporate redirection web site
I’ve finally migrated my corporate URL redirection service from an handwritten MSFT-IIS-ASP solution to a new BSD jailed system running a Drupal instance. The new solution empowers the Front Page, the Path Redirect and Web file Manager modules, and enables all authorized users to both maintain all the official URL redirects and manage a dedicated WebFM file repository, from anywhere their are working.
The base URL of the new service is http://go.valsania.it.
wpDirAuth
I finally got the time to make the wpDirAuth plugin function both on WordPress 2.5.1 and WordPress µ 1.5.1. My need is to migrate to the WPMU platform from Telligent’s Community Server as soon as possible, since I’m planning to port my entire corporate infrastructure from MSFT to the more dependable BSD Unix technology.
Unfortunately the 1.2 version of this plugin simply didn’t work on the latest versions of WP, so I had to apply the Patch for WordPress 2.5 compatibility kindly published by Adam Yearout. As now, I’ve only got the time to test it against Microsoft Active Directory LDAP servers, but I plan to try it in an Apple Open Directory environment before put it in production. The pilot blog collection can be accessed at the well-known Valsania Corporate Blogs WMPU instance.
UPDATE:
I’ve just tried to bind against an Apple Open Directory LDAP service, and the process is quite straightforward: the only real difference is the user object’s attribute to search for to identify the user who is logging in (sAMAccountName for AD, uid for OD), ad shown in the following image.
As you see, in this example we have an OD domain named mydomain.local, and we are using the unprivileged user named dsquery to bind to the LDAP service.
NOTE: remember to populate the EMailAddress attribute of your users in Open Directory, if you whish to the required E-mail field in WordPress user profile to be automatically filled upon the first logon.